
AI Feels Smarter Because the System Is
A better experience must mean a smarter model. A more helpful response must mean the model is learning. This assumption is natural, but it is also incomplete.
Fluency Security
Security Research
Autonomy depends on strong detection.
Fluency’s behavioral analytics, UEBA clustering, and gap detection give both people and AI an unmatched ability to identify and resolve issues before they escalate.
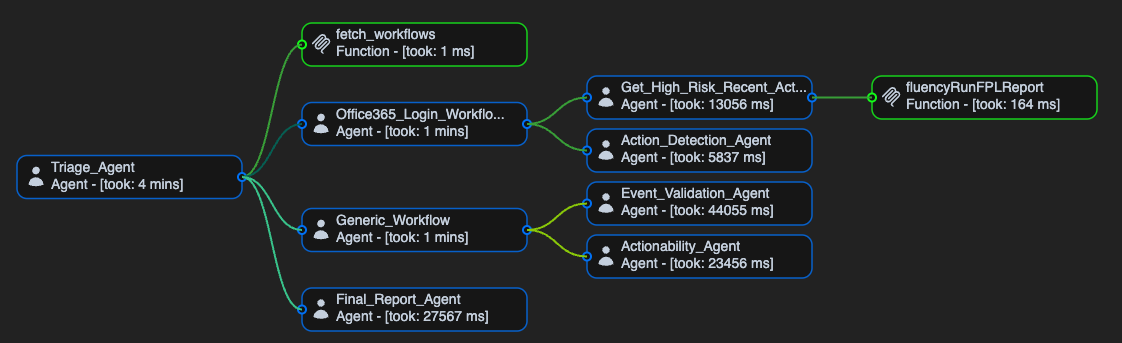
Everyone has seen this before. You log into an application after a long time and receive an email saying, "New login detected." Your bank asks whether a recent charge looks suspicious.
Nothing was blocked. Nothing necessarily went wrong. But something happened differently than normal, and the system noticed. That is behavioral detection.
Most endpoint and email security tools do not work this way. They rely on signatures, policies, and known-bad activity. They are not designed to understand how behavior changes over time. This is why organizations use Fluency — to continuously observe users, systems, and networks and highlight meaningful deviations that prevention tools cannot see.
Video Introduction
Watch our introduction video to discover how Fluency's AI SIEM transforms security operations with autonomous workflows and real-time analytics.
See how behavior enables autonomy
Autonomy does not come from automation alone. It comes from understanding. Fluency's behavioral analytics identify meaningful changes — first-time activity, abnormal access patterns, impossible travel, unusual timing, and deviations that require judgment. Once those behaviors are understood and grouped into context-rich cases, AI workflows can safely take action. This is why Fluency can operate autonomously where traditional SOAR platforms cannot. The system is not reacting to isolated alerts — it is reasoning over behavior.
Traditional SIEMs depend on databases — slowing down detection and overwhelming analysts with noise. Fluency takes a different approach. By processing data in-stream with machine learning security analytics, Fluency delivers instant detection, behavioral threat detection, and automated incident response capabilities that match the pace of your business.
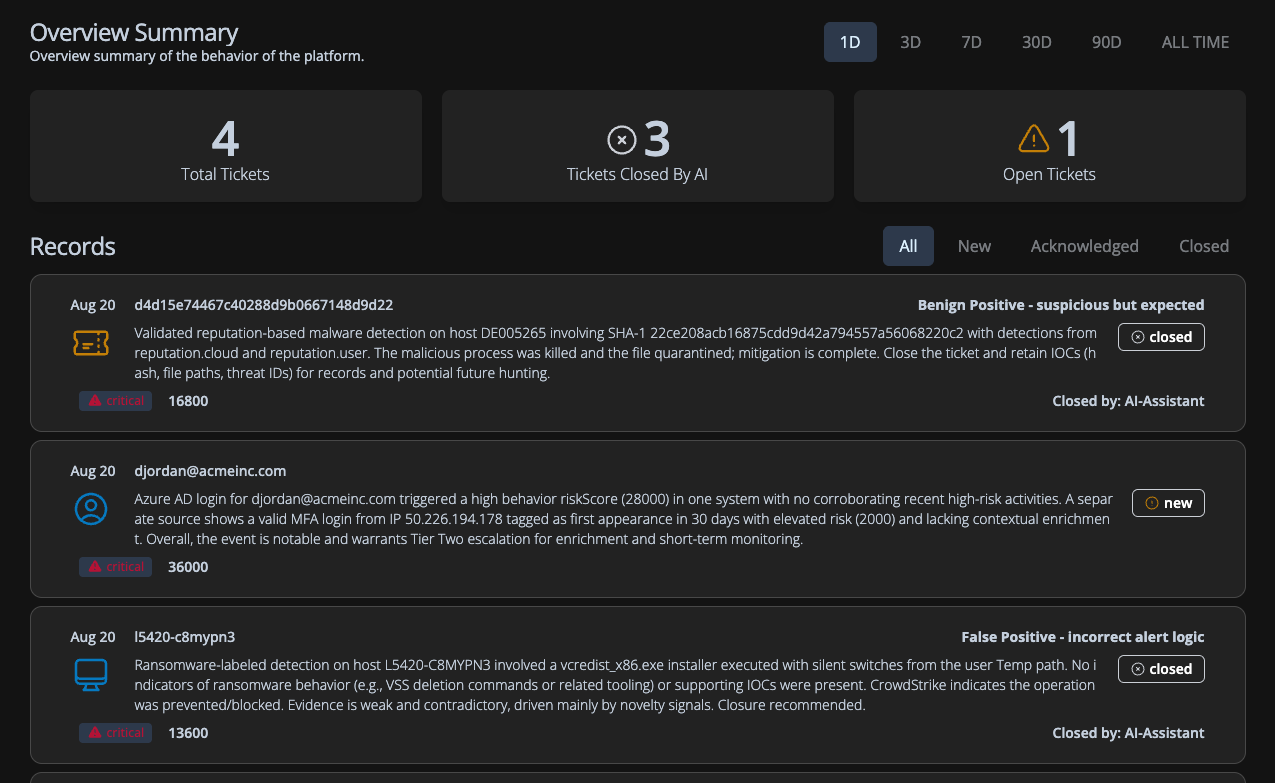
Fluency's AI workflows accelerate mean-time-to-analyze (MTTA) by guiding investigations and reducing manual effort, so analysts resolve issues faster and with greater accuracy.
By cutting false positives and automating repetitive tasks, Fluency lowers operational costs while increasing analyst effectiveness — delivering measurable value from day one.
Fluency adds identity and behavior context to every alert, allowing analysts to focus on high-impact issues instead of wasting time chasing noise.
Fluency is built to support the smallest organizations as well as global enterprises, ensuring advanced detection and response is accessible to all.
Easily connect to existing tools, data sources, and workflows without disruption, making deployment quick and adoption frictionless.
From startups to multinational corporations, Fluency scales effortlessly with your growth — maintaining performance without added complexity.
Insights & Research
Stay up-to-date with the latest insights on AI-driven security, SIEM technology, and cybersecurity operations from our security experts.

A better experience must mean a smarter model. A more helpful response must mean the model is learning. This assumption is natural, but it is also incomplete.
Fluency Security
Security Research
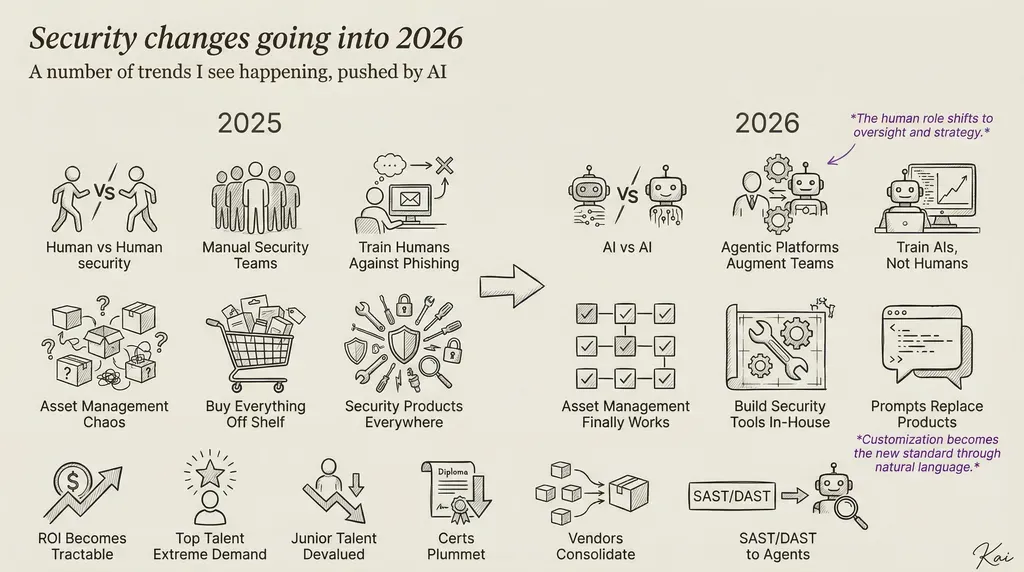
Daniel Miessler wrote one that genuinely stood out, "Cybersecurity Changes I Expect in 2026: My thoughts on what's coming for Cybersecurity in 2026". I read it first thing in the morning, which says a...
Fluency Security
Security Research

Ingext Community Edition is now available as a self-hosted, Kubernetes-based deployment, distributed using Helm charts. This release makes Ingext platform independent and accessible across multiple cl...
Fluency Security
Security Research
Don't Take Our Word for It—Experience Fluency Yourself. Share a little about your environment and our team will tailor a demo around your goals.
"Fluency has consistently met our company's IT needs and has provided extensive support in handling cybersecurity attacks. This is why we choose to renew our contract with them. It has proven to be a valuable investment."