
The More You Know, the Less You Trust AI, And That’s the Problem
A new study shows the more you know about AI the less you trust it—what that really means for hype, adoption, and the coming AI bubble.
Fluency Security
Security Research
Consistent, accurate detection — 24/7, without analyst fatigue.
By applying AI workflows directly to investigation and triage, Fluency delivers results with greater consistency and accuracy — even in the middle of the night when human teams are offline. That means higher-quality detection and response without expanding headcount, giving your organization a stronger security posture with fewer resources.
See Fluency in Action
Watch our introduction video to discover how Fluency's AI SIEM transforms security operations with autonomous workflows and real-time analytics.
Traditional SIEMs depend on databases — slowing down detection and overwhelming analysts with noise. Fluency takes a different approach. By processing data in-stream, Fluency delivers instant detection, context-rich alerts, and built-in scalability that matches the pace of your business.
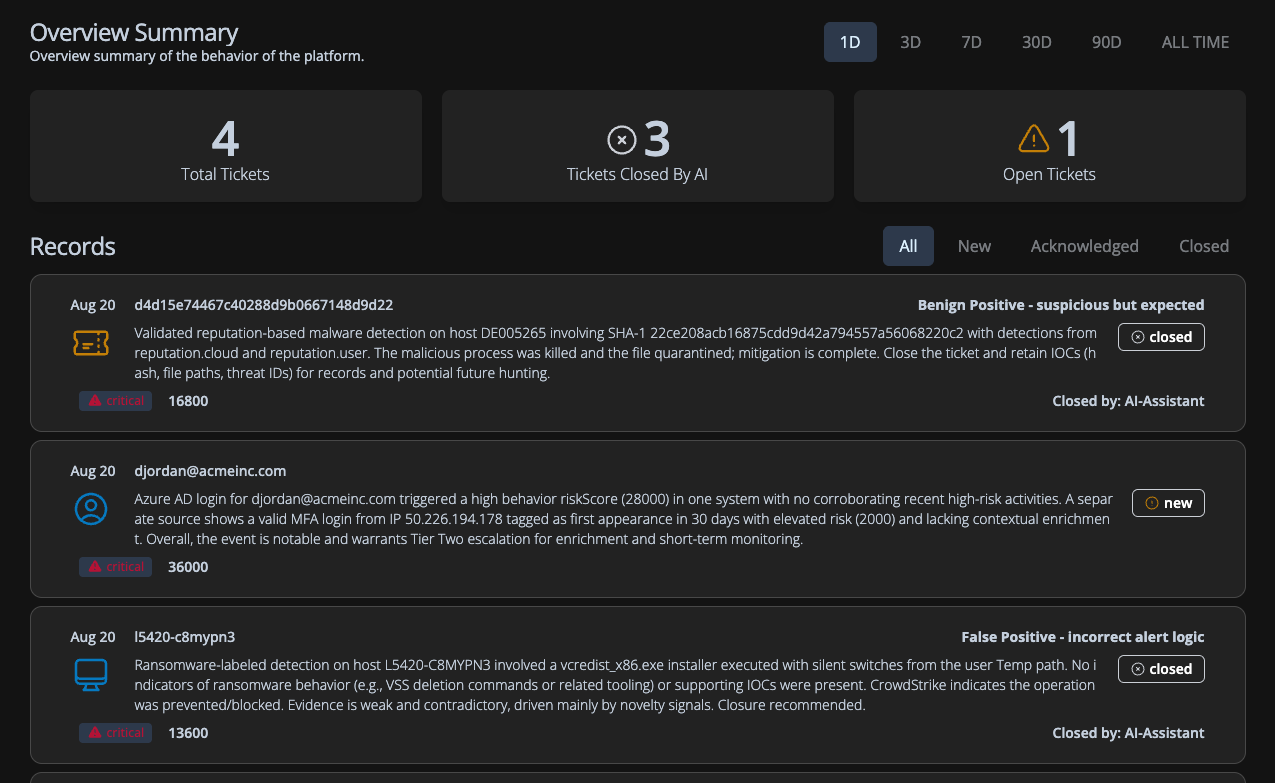
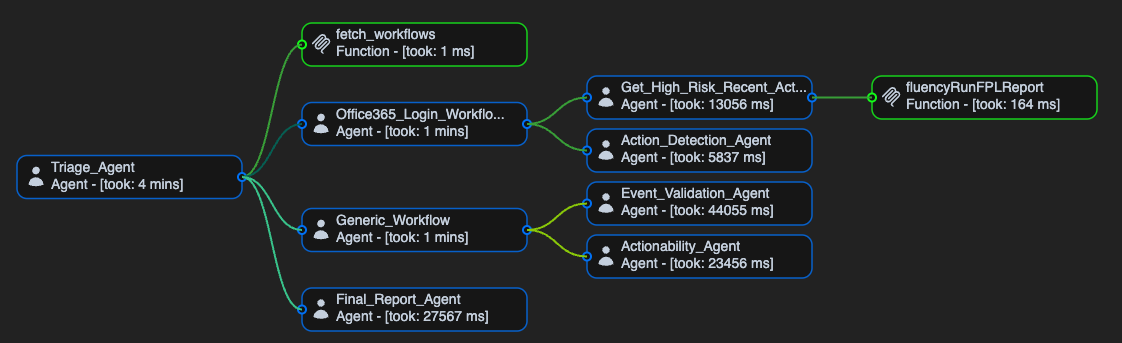
How is AI used in Fluency AI SIEM?
Discover how Fluency, the AI SIEM, transforms security operations. By processing billions of logs into a handful of meaningful cases, Fluency’s Orchestrator and AI-driven workflows replace endless alerts with clear, actionable insights. Unlike rigid SOAR playbooks, Fluency adapts to unexpected patterns, guiding junior analysts and empowering experts to focus on the hardest problems. The result: higher quality detection, fewer false alarms, and a smarter path to the Autonomous SOC.
Latest from Fluency Security Blog
Stay up-to-date with the latest insights on AI-driven security, SIEM technology, and cybersecurity operations from our security experts.

A new study shows the more you know about AI the less you trust it—what that really means for hype, adoption, and the coming AI bubble.
Fluency Security
Security Research

This article addresses a rising skepticism about whether vendors are sufficiently transparent, accountable, and secure.
Fluency Security
Security Research

The real value of a SIEM isn’t in storing data, it’s in the process of transforming, interpreting, and routing that data into something usable for security operations.
Fluency Security
Security Research
Don’t Take Our Word for It—Experience Fluency Yourself.
“Fluency has consistently met our company’s IT needs and has provided extensive support in handling cybersecurity attacks. This is why we choose to renew our contract with them. It has proven to be a valuable investment.”